How to turn Hazel into a security guard for your Mac
This is part 2 of a 3-part series on Mac data security: Perils of persistent data.
* * *
 Hazel is one of the most boring, yet amazing applications for the Mac in existence. Even if used lightly, it can yield huge benefits to anyone that likes to be more organized without having to lift their own fingers.
Hazel is one of the most boring, yet amazing applications for the Mac in existence. Even if used lightly, it can yield huge benefits to anyone that likes to be more organized without having to lift their own fingers.
I’ve talked before about how I use Hazel geekery to automate web writing. I’m also using it to securely delete files that have sensitive financial data.
For me, Hazel is more than a maid. She’s a security guard too.
In this post, I'll discuss how I use Hazel to securely delete
- Quicken files
- Files with a color label
- Files copied to a specific folder
- Files containing specific words
Shredding downloaded Quicken files
I use Quicken Essentials for Mac (QEM) to keep up with my basic personal finance information. By default, I have all of my web browsers set to download files to my Downloads folder. So every time I let QEM download account information, it puts a QFX file inside Downloads.
For a while, I didn’t think anything of this.
One day, I decided to crack open one of those files to see what is inside. (They can be viewed in any text editor.) I was a little surprised to see that each one contained a full account number for the associated account.
I don’t really care that much about someone seeing the balances or transactions in my checking account, but I’d rather not leave a trail of account numbers lingering on my hard drive.
Before I used Hazel, I had been letting these QFX files pile up in my Downloads folder – along with a lot of other junk.
It’s really easy to configure Hazel to clean out your Downloads folder on a regular basis. Just like any other folder, when Hazel “deletes” files, it simply moves the files to the Trash folder on your Mac. It doesn’t permanently remove the files from your system.
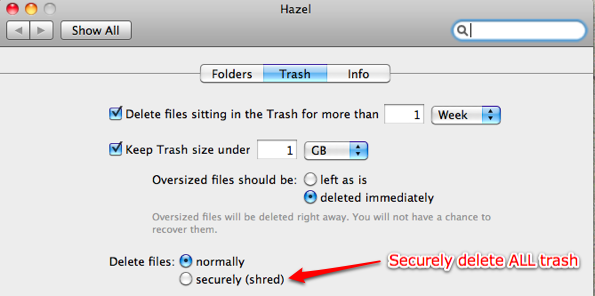
For permanent file and folder removal, the primary option Hazel offers is secure deletion of the Trash folder contents (all at once).
Effecting the selective, secure delete
Personally, I don’t want Hazel to do a secure delete each time it empties my Trash folder, mainly because it adds run time. But really, it just reeks of OCD, overkill, hyper-paranoia behavior. And sometimes I send a lot of media files to the Trash at once, so I don’t want the system unnecessarily chewing away on those.
I wanted a more surgical zapping approach (because that’s not obsessive at all, right?) where I single out specific files that I want to be securely deleted. Turns out, it’s easy.
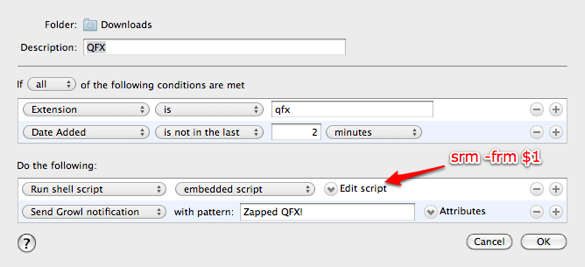
Instead of telling Hazel to move “sensitive” files to the Trash, I tell it to fire off a super-simple little shell script that I stumbled across in a thread over at Hazel's forum.
srm -frm $1Here’s an explanation of what this command does:
- srm is the secure remove command common to all Unix and Unix-like systems, including Macintosh.
- f forces the removal of the file (no questions asked).
- r tells srm to be recursive (remove contents of subfolders).
- m is the “medium” security option. It tells srm to do a 7-pass delete, meaning that it wipes over the file 7 times – like a cross-cut paper shredder. Most of the time, I think this is plenty. If you leave off m, srm will do a 35-pass delete and take a lot longer to run.
- $1 represents the file(s) to be shredded
Now is a good time to issue the standard secure delete disclaimer: there is no undo on this action. It will delete the file permanently. No going back. But remember, that’s the goal here, right?
If you’re comfortable with those powerful, little letters above, all you have to do is paste the command into the “Run shell script” box in the “Do the following” section of your Hazel rule.
This rule instructs Hazel to zap any file with a QFX extension about 2 minutes after it lands in the Downloads folder. With Hazel in control, I no longer have to even think about getting rid of these pesky files. They just go away – securely.
Securely shredding miscellaneous files that land in your Downloads folder
I routinely download bank statements, and just like their paper ancestors, they have my full account number printed clearly at the top of the page.
Unlike the Quicken files I just mentioned, most of the financial statements I download are in PDF format. I don’t want to set up a rule to annihilate every PDF file in my Downloads folder since I work with tons of other non-sensitive PDF.
The naming scheme banks use for downloadable statements aren’t consistent either. I’ve decided that the best way to get rid of PDF containing account numbers is simply mark them for execution using a gray color label.
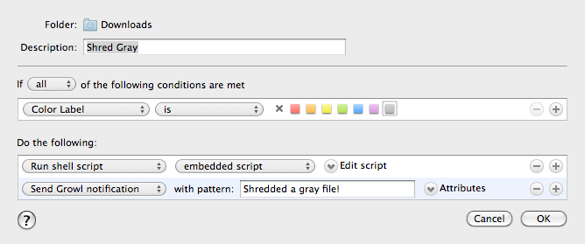 I like the color label approach because I can use it on more than one file at once. If I download, say, 3 statements, I can quickly color them for death by selecting all 3, then choosing the gray color label under Finder’s File menu. (I would love to find a keyboard shortcut for bringing up the color label selector, but I haven’t yet.)
I like the color label approach because I can use it on more than one file at once. If I download, say, 3 statements, I can quickly color them for death by selecting all 3, then choosing the gray color label under Finder’s File menu. (I would love to find a keyboard shortcut for bringing up the color label selector, but I haven’t yet.)
Using Hazel to create a shred bin
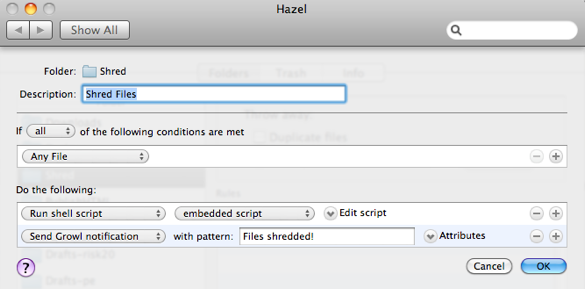
Hazel can watch any folder on your Mac and do all sorts of things as files are added and changed. You can take advantage of Hazel’s voyeuristic ways by creating a folder specifically for shredding any files that land in it. Think of it like the paper shredder sitting next to your regular trash can at home.
We can use the same simple shell script we used above to create a rule for zapping anything we drag and drop into our Shred folder:
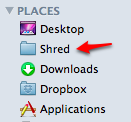
The Shred folder approach has the advantage of being available anywhere. I put a shortcut to mine in my Finder sidebar so that I can simply drag files into it from any folder.
Remember, the Shred folder is an abyss. Anything you toss into it (intentionally or not) is gone for good.
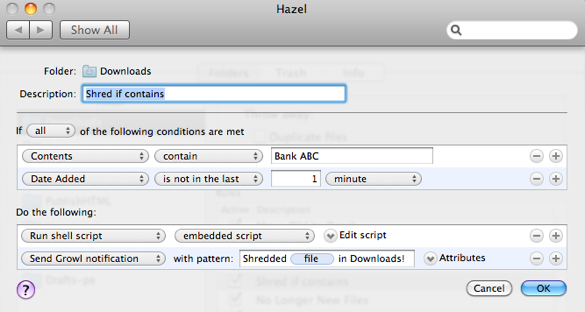
Secure deleting based on file contents
Suppose you bank with Bank ABC. Every statement you download from Bank ABC’s site has their name on it.
For a really hands-off solution, you could create a Hazel rule to annihilate any file containing Bank ABC maybe 5 or 10 minutes after being downloaded. This would give you plenty of time to copy it to a secure location or do something else with it.
Next up
In the next and final part of this series, I’ll describe the process I use for long-term storage of sensitive files.